Refer to the Wi-Fi Protected Setup Specification Version 1.0h standard.
WiFi Protected Setup (WPS) allows users to set up and expand the WiFi networks with security enabled, even if they are not familiar with the underlying technologies or processes involved. For example, users no longer have to know that SSID refers to the network name or WPA2 refers to the security mechanism.
WPS does not support ad hoc networks.
WPS will configure the network name SSID and security key for the AP and WPS client devices on a network. It supports the WEP / WPA / WPA2 security methods.
2 methods are supported
- WPS-PBC (Push Button Configuration)
Users can connect the device (MRF24WG0M) to the network and enable data encryption by pushing the buttons on the AP and client device. Users do NOT need to know the SSID of the AP, however the users are required to be within close proximity of the AP to press the push button on the AP.
- WPS-PIN (Personal Information Number)
PIN is provided for each device which joins the network. Enter this PIN on the AP/Router (Registrar) and activate AP (Registrar) first before MRF24WG0M attempts to connect. The last digit of the PIN is the checksum of the first 7 digits of the PIN. This checksum must be correct, otherwise MRF24WG0M module will reject the PIN code.
To set up WPS-PBC, define
- MY DEFAULT_NETWORK_TYPE as CFG_WF_INFRASTRUCTURE
- MY_DEFAULT_SSID_NAME as ""
- MY_DEFAULT_WIFI_SECURITY_MODE as WF_SECURITY_WPS_PUSH_BUTTON
To set up WPS-PIN, define
- MY DEFAULT_NETWORK_TYPE as CFG_WF_INFRASTRUCTURE
- MY_DEFAULT_SSID_NAME to be the same SSSID as the AP/router
- MY_DEFAULT_WIFI_SECURITY_MODE as WF_SECURITY_WPS_PIN
- MY_DEFAULT_WPS_PIN to be the same as the AP/router PIN.
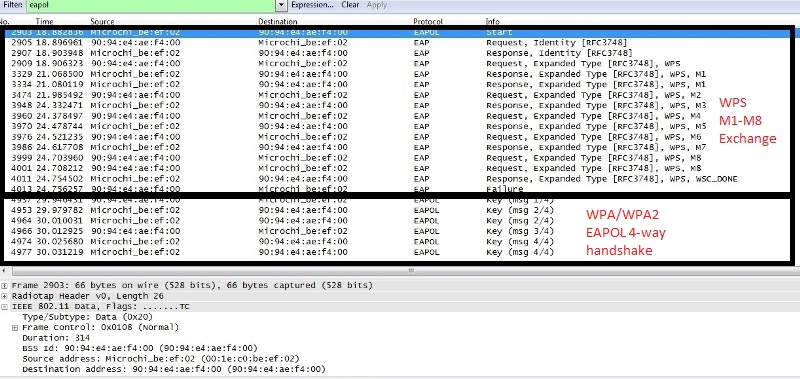
WPS protocol can be viewed as a security connection method, built upon the existing security modes WPA/WPA2. The protocol encompasses a M1-M8 message exchange process. Therefore additional time is consumed. The WPS specification specifies below:
- Retransmission timeout = 5 sec
- Individual message processing timeout = 15 sec
- Overall timeout for entire protocol to complete = 2 min
To address this lengthy time required every single time the MRF24W is restarted, the function prototype WF_SaveWPSCredentials() can be invoked. Basically what this function does is to retrieve WPS credentials from MRF24W and store these into global variable AppConfig. In this way, it makes the WPS credentials re-useable and shorten subsequent reconnection time. For an actual product, it is advised to add in a timeout such that the WPS credentials will need to be refreshed or updated periodically.
WPS protocol
The WPS protocol, which encompass WPA/WPA2 authentication process, involves key derivation from the given passphrase. Since this key derivation process is computational intensive and requires memory space, options are given
- Host to derive the key from the passphrase
DERIVE_KEY_FROM_PASSPHRASE_IN_HOST needs to be enabled. Refer to function prototype pbkdf2_sha1() in WF_pbkdf2.c for the algorithm.
In this scenario, WF_YieldPassphrase2Host() will inform MRF24W that host wants to do conversion. MRF24W will generate an event (WF_EVENT_KEY_CALCULATION_REQUEST) to host (eg PIC32) and set g_WpsPassphrase.valid to TRUE. Upon receipt of this event, the host will execute the function WF_ConvPassphrase2Key() to convert the passphrase to key. Upon completion of this conversion, the host will call WF_SetPSK() to pass the converted key to MRF24W.
- MRF24W will handle the entire WPA/WPA2 passphase and then key derivation
MRF24WG0M will consume about ~25 seconds.
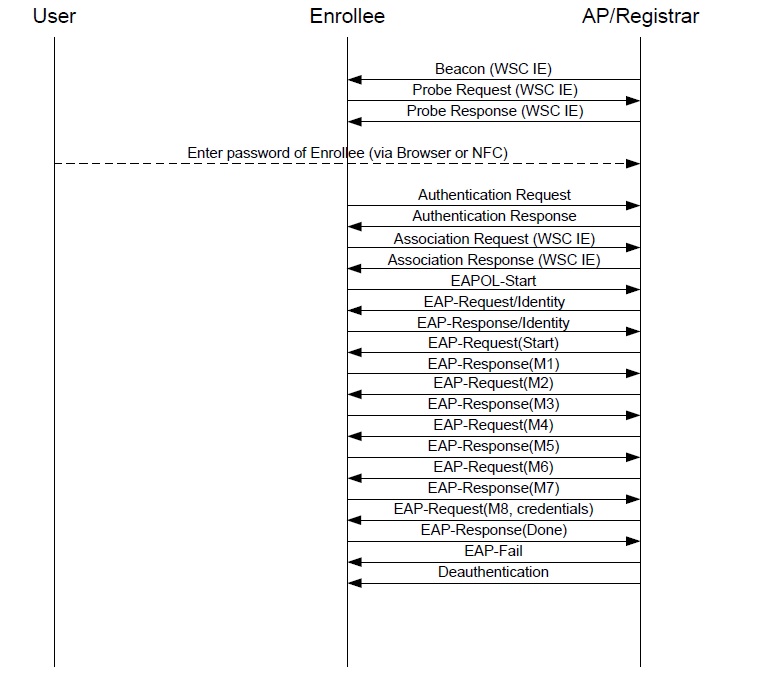
Upon initial connection (after authentication followed by association), WPS will take place and is performed over 2 phases.
Phase A: WPS Frame Exchanges (EAP authentication protocol)
Refer to Wi-Fi Simple Configuration Specification Version 2.0.2 or Wi-Fi Protected Setup Specification Version 1.0h “Figure 4: In-band Setup Using a Standalone AP/Registrar”.
Information and network credentials, such as SSID, security mode, security keys, security passphrase, etc, are securely exchanged over the air using the Extensible Authentication Protocol (EAP). From these WPS frame exchanges, WPS will automatically configure the network connection, without having the user to know the SSID and security keys or passphrases, etc.
The enrollee is defined as a device seeking to join a wireless network and is represented by MRF24WG0M. In the infrastructure network, the enrollee and wireless client are synonymous.
WSC IE (Wi-Fi Simple Configuration Information Element) will be present in the beacons, probe request/responses frames and association request/response frames. Refer to Wi-Fi Simple Configuration Specification for details on the WSC IE contents.
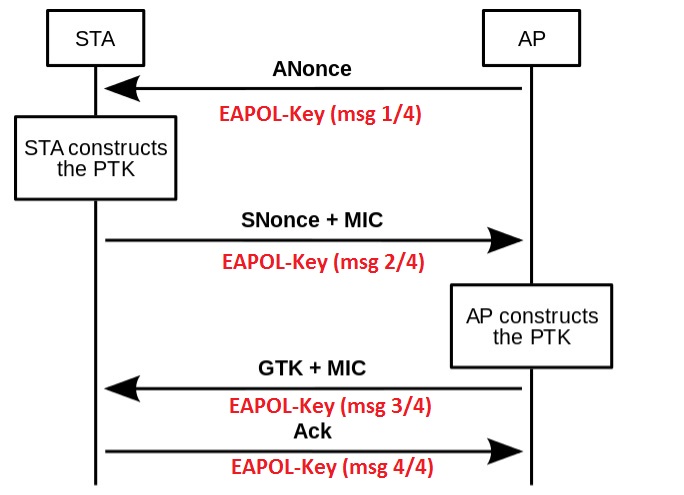
Phase B: EAPOL 4-way Handshake or 802.1X-authentication
Refer to specifications IEEE 802.11i-2004: Amendment 6: Medium Access Control (MAC) Security Enhancements.
After a successful EAP authentication, the EAPOL 4-way handshake begins.
The supplicant, STA and wireless client are synonymous.
Likewise, the authenticator and AP/router are synonymous.
The 4-way handshake shares unique random information between the supplicant/client and the authenticator /AP to derive the PTK key.
Below is a brief description of the EAPOL 4-way handshake
4-way handshake message 1
The AP/router sends the STA a nonce (ANonce). Along with this ANonce, the frame includes the AP/router MAC address. At this point the STA has all the information needed to create the PTK; Anonce, AP/router MAC address, its own Snonce and MAC address.
4-way handshake message 2
The STA creates its nonce (SNonce). The STA can now calculate the PTK because it has all the information from the first handshake. In this second message, the STA sends the SNonce to the AP/router. The STA also sends the security parameters (RSN) information. The entire message gets an authentication check using the (MIC) from the pairwise key hierarchy. The AP/router can then verify that the information, including the security parameters sent at association is valid.
4-way handshake message 3
In this third message, the AP/router derives the GTK key from the GMK key. The AP/router derives an ANonce, RSN information element info and a MIC and sends these information to the STA in an EAPOL-Key frame. This is kept secret from sniffing since it is encrypted within the PTK.
4-way handshake message 4
The fourth message acts as a confirmation. It indicates that the temporal keys are installed.
Below shows the WPS protocol
Integration of WPS into 802.11 joining operation
Below lists the overall sequences
• Scanning, Authentication, Association
• WPS Frame Exchanges (EAP protocol)
• Deauthentication (Refer to above figure) or Disassociation
o Some APs are found to transmit disassociation instead of deauthentication frame.
Provision needs to be made to handle receipt of disassociation frame.
• Authentication, Association
• EAPOL 4-way handshake or 802.1X-authentication
|
|
Name |
Description |
 |
Gets the WPS credentials for the specified Connection Profile ID for MRF24WG0MA/B. | |
 |
Allows host to handle WPS WPA/WPA2-PSK passphrase | |
 |
Sends PSK to module FW in WPS mode. | |
 |
Stores WPS credentials into global variable AppConfig | |
 |
Configures WEP security mode from WPS credentials data |
|
|
Name |
Description |
 |
This is type tWFWpsCred. |