Trust Relationships
Trust relationships allow multiple domains to be logically connected and allow users to be authenticated on their primary domain, yet gain access to resources connected to other domains without having to sign-on again to these other domains. Using Trust relationships to connect domains, network designers can build extremely large and complex networks.
Trust relationships are easy to administer and facilitate:
- Centralised administration in multiple domain models.
- User logons from domains where they do not have accounts.
- Users from one domain to access resources in another domain, even if they do not have an account in that domain.
- Networks with larger numbers of users, by locating machine and resource accounts in other domains.
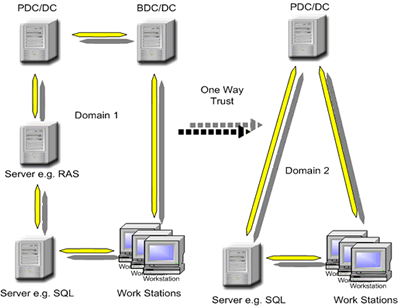
One- and Two-Way Trust Relationships
Trust relationships can be one- or two-way. The diagram above illustrates a one-way Trust relationship; Domain1 is trusting Domain2. I.e. All users from the trusted domain (Domain2) can access resources connected to the trusting domain (Domain1).
A two-way trust exists where both domains trust each other equally (see diagram below). Two-way trusts allow users defined in Domain1 and Domain2 to access resources connected to either domain.
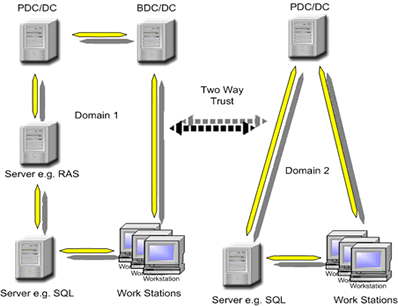
One of the main considerations is that security on a trusting domain can be easily undermined by weak security standards and practices on a trusted domain.
Notes on Trust Relationships
A trust relationship is a link between two domains where the trusting domain honours logon authentications for the trusted domain.
Active Directory services support two forms of trust relationships: one-way, non-transitive trusts and two-way, transitive trusts.
In a one-way trust relationship, if Domain A trusts Domain B, Domain B does not automatically trust Domain A.
In a non-transitive trust relationship, if Domain A trusts Domain B and Domain B trusts Domain C, then Domain A does not automatically trust Domain C.
Networks running Windows NT 4.0 and earlier versions of Windows NT use one-way, non-transitive trust relationships. You manually create one-way, non-transitive trust relationships between existing domains. As a result, a Windows NT 4.0 (or earlier Windows NT) network with several domains requires the creation of many trust relationships.
Active Directory services support this type of trust for connections to existing Windows NT 4.0 and earlier domains and to allow the configuration of trust relationships with domains in other domain trees.
A two-way, transitive trust is the relationship between parent and child domains within a domain tree and between the top-level domains in a forest of domain trees. This is the default for Windows 200X. Trust relationships among domains in a tree are established and maintained automatically. Transitive trust is a feature of the Kerberos authentication protocol, which provides for distributed authentication and authorization in Windows 200X.
In a two-way trust relationship, if Domain A trusts Domain B, then Domain B trusts Domain A. In a transitive trust relationship, if Domain A trusts Domain B and Domain B trusts Domain C, then Domain A automatically trusts Domain C. Therefore in a two-way, transitive trust relationship, if Domain A trusts Domain B and Domain B trusts Domain C, then Domain A trusts Domain C and Domain C trusts Domain A.
If a two-way, transitive trust exists between two domains, you can assign permissions to resources in one domain to user and group accounts in the other domain, and vice versa.
Two-way, transitive trust relationships are the default in Windows 200X. When you create a new child domain in a domain tree, a trust relationship is established automatically with its parent domain, which imparts a trust relationship with every other domain in the tree. As a result, users in one domain can access resources to which they have been granted permission in all other domains in a tree.
Note, however, that the single logon enabled by trusts does not necessarily imply that the authenticated user has rights and permissions in all domains.
The trusting domain will rely on the trusted domain to verify the user accounts and passwords for users logging on the trusted domain.