Wireshark has two filtering languages: One used when capturing packets, and one used when displaying packets. In this section we explore that second type of filter: Display filters. The first one has already been dealt with in Section 4.13, “Filtering while capturing”.
Display filters allow you to concentrate on the packets you are interested in while hiding the currently uninteresting ones. They allow you to select packets by:
-
Protocol
-
The presence of a field
-
The values of fields
-
A comparison between fields
-
... and a lot more!
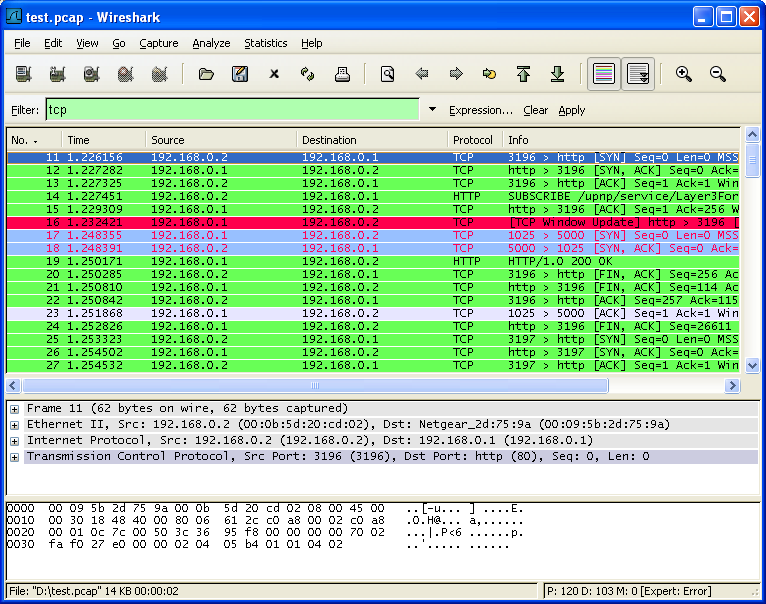
To select packets based on protocol type, simply type the protocol in which you are interested in the Filter: field in the filter toolbar of the Wireshark window and press enter to initiate the filter. Figure 6.6, “Filtering on the TCP protocol” shows an example of what happens when you type tcp in the filter field.
![[Note]](note.png)
|
Note! |
|---|---|
|
All protocol and field names are entered in lowercase. Also, don't forget to press enter after entering the filter expression. |
As you might have noticed, only packets of the TCP protocol are displayed now (e.g. packets 1-10 are hidden). The packet numbering will remain as before, so the first packet shown is now packet number 11.
![[Note]](note.png)
|
Note! |
|---|---|
|
When using a display filter, all packets remain in the capture file. The display filter only changes the display of the capture file but not its content! |
You can filter on any protocol that Wireshark understands. You can also filter on any field that a dissector adds to the tree view, but only if the dissector has added an abbreviation for the field. A list of such fields is available in Wireshark in the Add Expression... dialog box. You can find more information on the Add Expression... dialog box in Section 6.5, “The "Filter Expression" dialog box”.
For example, to narrow the packet list pane down to only those packets to or from the IP address 192.168.0.1, use ip.addr==192.168.0.1.
![[Note]](note.png)
|
Note! |
|---|---|
|
To remove the filter, click on the Clear button to the right of the filter field. |