Authentication is the process of verifying the identity of a user or service trying to access an Amazon Web Services (AWS) product. Access Control defines who can access objects and buckets within Amazon S3 and the type of access (e.g., READ, WRITE, and so on). Authentication combined with access control prevents unauthorized users from accessing your data, modifying your data, deleting your data, or using your AWS account for services that cost you money.
Every interaction with Amazon S3 is authenticated or anonymous. When you sign up for an AWS account, you are provided with an AWS Access Key ID and a Secret Access Key. When you perform a request with Amazon S3, you assemble the request, perform a hash on the request using your Secret Access Key, attach the Signature (hash) to the request, and forward it to Amazon S3. Amazon S3 verifies the Signature is a valid hash of the request and, if authenticated, processes the request.
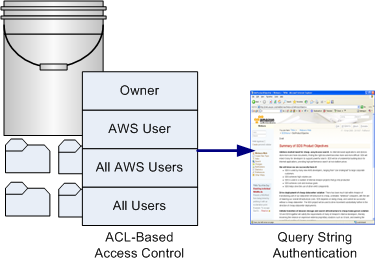
To allow selected users to access objects or buckets in your Amazon S3 account, you can use access control lists (ACLs) or query string authentication.
ACLs allow you grant access to specific AWS users, all AWS users, or any user through anonymous access. When granting access to a specific AWS user, the user must have an Amazon account and must be signed up for AWS and Amazon S3. This will enable the user to access any allowed buckets or objects using his AWS Access Key ID and Secret Access Key. When you grant access to all AWS users, any AWS user will be able to access allowed buckets or objects using an AWS Access Key ID and Secret Access Key. When you grant anonymous access, any user will be able to access allowed buckets or objects by omitting the AWS Access Key ID and Signature from a request.
Any user that is granted access to an object or bucket can construct an HTTP URL that can be used to access that object or bucket through the query string authentication mechanism. This HTTP URL can be distributed to any user with a web client or embedded in a web page.
![[Note]](note.png)
|
Note |
|---|---|
|
All HTTP queries have an expiration parameter that allows you to set how long the query will be valid. For example, you can configure a web page graphic to expire after a very long period of time or a software download to only last for 24 hours. |