Authenticate
Navigation Path: Tag Operations > Authenticate
The “Authenticate” Tab is used to both insert and activate keys, as well as authenticate tags and obtain encrypted data using those keys.
Activating Keys
Two 16-byte keys are inserted into specific User memory locations, and are activated by writing a specific value into two other User memory locations. The keys may be freely read and edited until activated, at which point those memory locations become inaccessible. The two keys are called "Key0" and "Key1". Either may be used for authenticating the tag, but only Key1 may be used to decrypt data that has been encrypted by the tag.
The key insertion and activation is controlled by the top portion of the "Authenticate" tab. These are the expected results for a tag that has never had a key written to it.
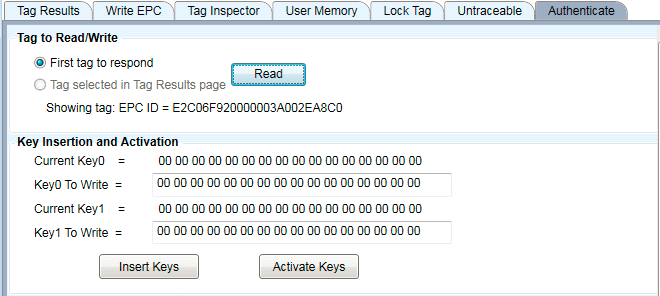
Figure 26: Default Unactivated Keys
Note that although the current value is shown with spaces between the bytes, you must enter the desired value without spaces, as shown here:
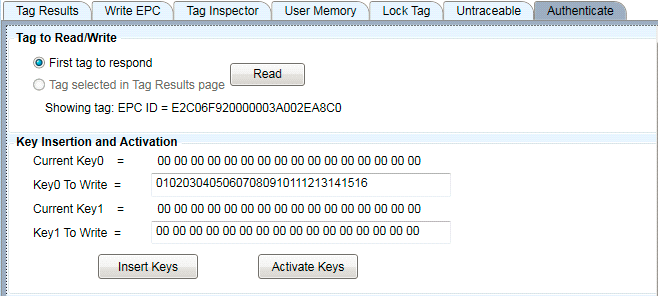
Figure 27: Entering a Key
When you press "Insert Keys", this pop-up message will be displayed:
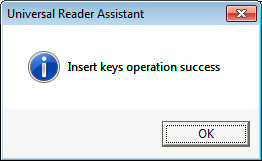
Figure 28: Success Message
Note that the Current Key values will remain unchanged until you press "Read" again".
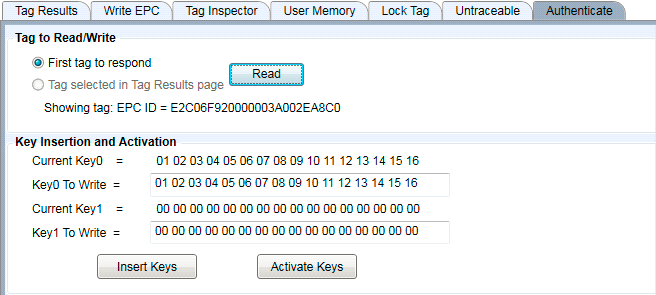
Figure 29: Key Confirmation
Always make sure you read the keys to confirm that the value is what you want before activating them. Once activated, you cannot change the keys nor determine their current value. If you read a tag whose keys have been activated, you will get this result:
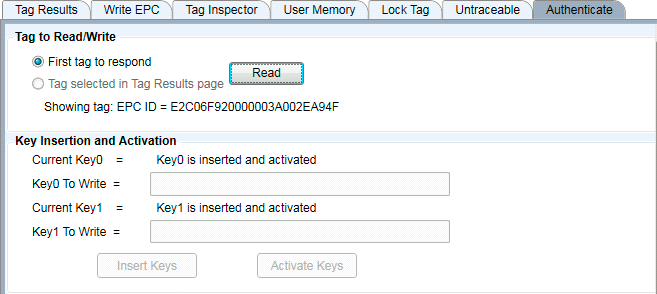
Figure 30: Obscuring of Keys Following Activation
Note that there is no provision for only activating one of the keys. If you leave any key at its default "0000..." value, it will be activated to that value.
Tag Authentication
Tags are authenticated by having the reader send a random challenge string to the tag, the tag uses its key to encrypt the challenge, and sends the result back. The reader then uses the key to decrypt the message and, if the decrypted message is the one it sent to the tag, it declares the tag authentic.
To authenticate the tag, enter key0 or key1 for the tag and press "Authenticate Key0" or "Authenticate Key1". You will see a success message and the same "Returned Challenge" value as the "Random Challenge" field above, as shown here:
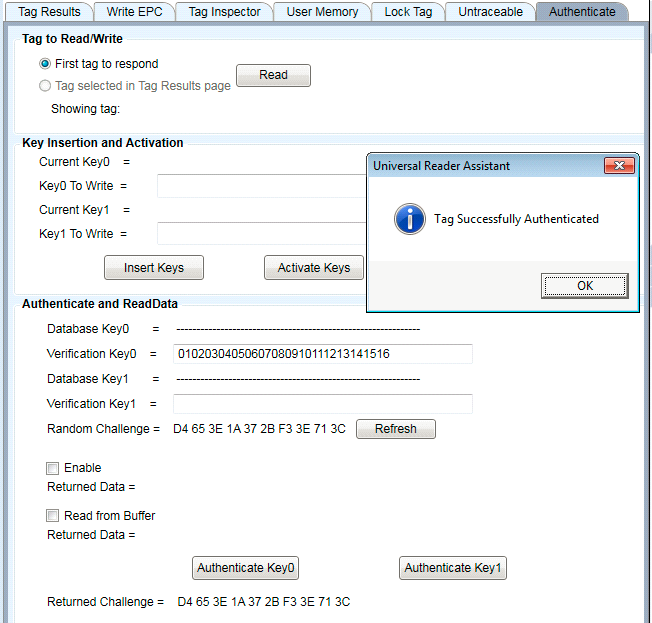
Figure 31: Successful Tag Authentication
Key1 may also be used for tag authentication.
If the key entered into the verification field does not match that in the tag, Universal Reader Assistant will still report that the Authentication Failed, as shown below. Note that the Returned Challenge will not match the Random Challenge value.
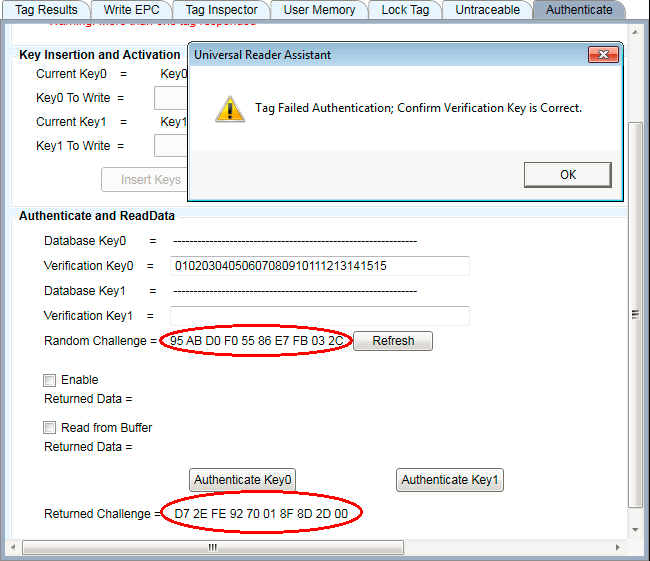
Figure 32: Failed Tag Authentication
If you want to do repeated trials with different Random Challenge values, press "Refresh" by the Random Challenge value and a new random value will be generated.
Obtaining Encrypted Data With Authentication
You may obtain encrypted data as well as authenticate the tag by selecting "Enable Returned Data" and selecting which memory location you want returned. Note that data is selected in 64 bit (2 Word) increments. As for Authenticate, the value returned is only valid if the Returned Challenge matches the Random Challenge, as shown here:
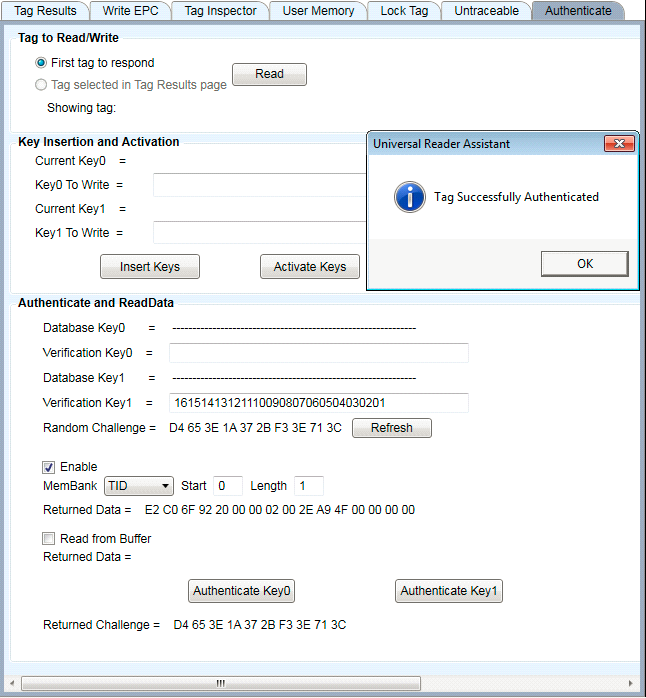
Figure 33: Successful Authentication with Returned Data
If the key used to decrypt the data does not match the one in the tag, the Returned Challenge will not match the Random Challenge and the data returned will not be valid. A message indicating that the authentication failed will be displayed as, shown below, and the Returned Challenge value will not match the Random Challenge value. The returned data will be incorrect, but displayed, so that the user can better understand how data encryption security works for Gen2V2 tags.
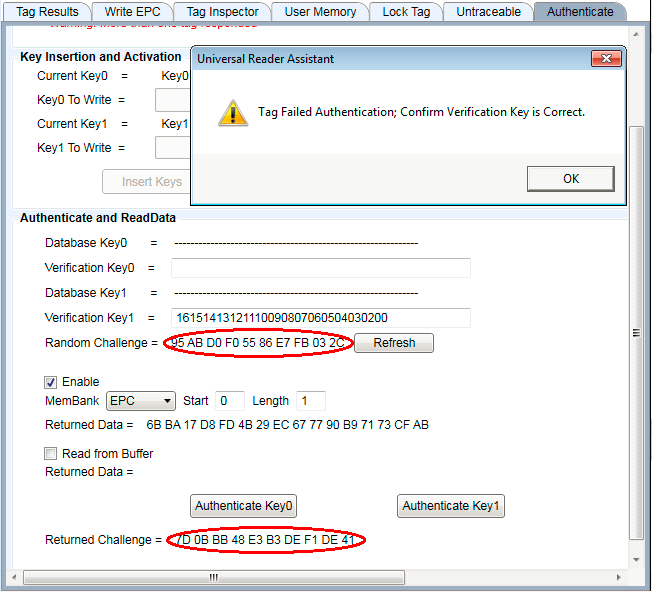
Figure 34: Authentication with Data Failure
Note that the Access Password is security is bypassed when encrypted data is being requested.
Obtaining Encrypted Data from Buffer
NXP tags have two options for obtaining encrypted data. The normal one is for the tag to backscatter the value. The other option is for the tag to put the data in a buffer for the reader to access. This access must be done before the tag is powered down, so cannot be used to obtain the data later. It is simply a different method for obtaining the data immediately.
This method of obtaining the data is activated by selecting "Read from Buffer". The returned data is displayed as shown here. As with the normal encrypted data read function, it is only supported for Key1.
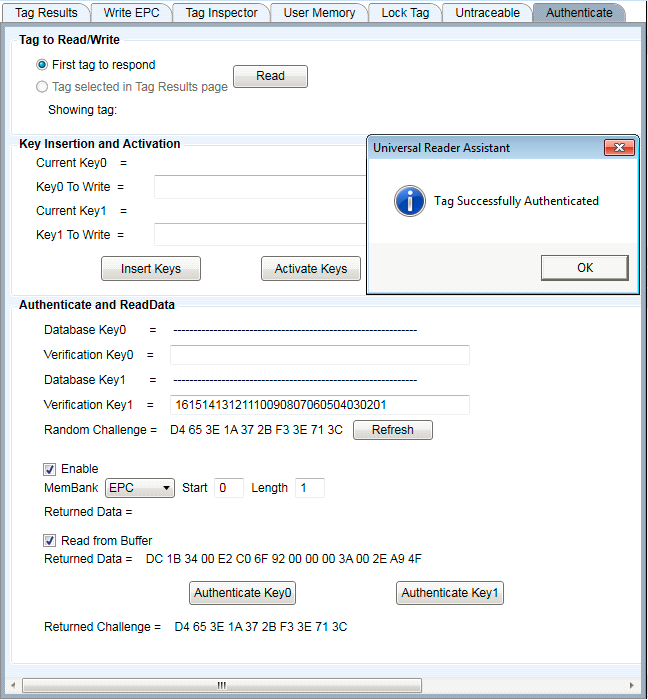
Figure 35: Authenticate with Buffer Data Read Success
If the key does not match the one programmed into the tag, the authentication will fail, and the following error message will be displayed:
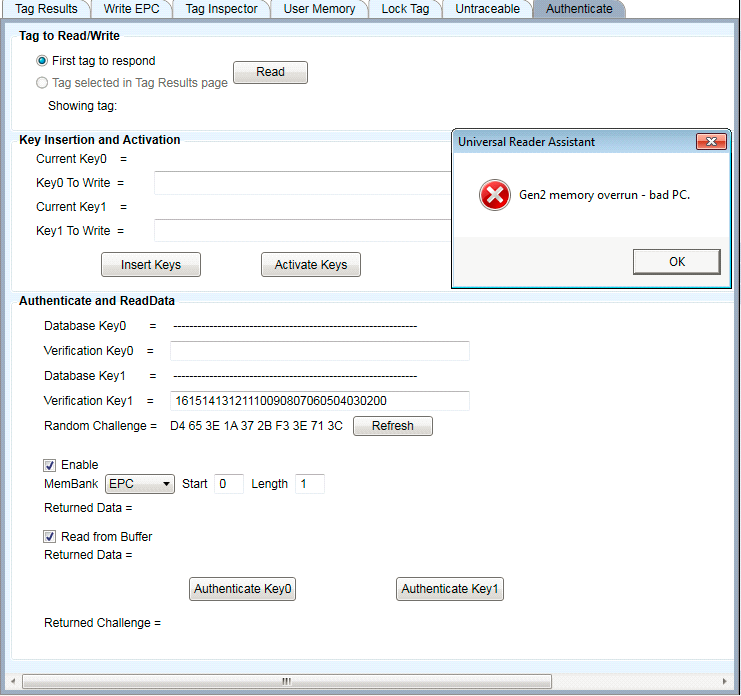
Figure 36: Failure of Authentication with Buffer Data Read
Note that the error message is a Gen2-level failure, not a failure detected upon comparison of the Returned Challenge and the Random Challenge, as was the case for non-buffer reads.