Traditionally applications were compiled to the native code of the target CPU. During this translation all the information about the source code was lost. However it is still possible to infer the program operation using debugging and hacking tools but it's difficult, time-consuming and very expensive craft.
In contrast, .NET applications are compiled to the CIL code. CIL code contains a lot of additional metadata which allows to achieve better interoperability and robustness of the application. But CIL metadata allows to infer program operation much easier at the same time. Using specially designed tools such as decompilers it is even possible to retrieve source code of the .NET application. So when .NET application published without being obfuscated it is equivalent to releasing its source code with all painful consequences.
Obfuscation removes redundant CIL metadata and scrambles and encrypts the rest. So after obfuscation it is much harder to dig in into obfuscated .NET application. However it is still possible to infer the program operation using specially designed tools but it is difficult, time-consuming and expensive now just as in case of the native code.
Let's perform some practical job to undercover the way your .NET application can be decompiled. First of all, we need some sample application
to dig in. Let me introduce one of superstar applications with ambitious title "My Precious Idea" as a sample. I should admit that this application
is based on the Mike's Gold port of the vintage "Space Invaders" game.
This C# application was compiled in Release configuration with Microsoft Visual Studio.
Here is the look of sample application when it is running:
Really nice, isn't it? To decompile the application we will use .NET Reflector tool. Then just open "My Precious Idea.exe" file with .NET Reflector. Here is what can be seen after opening:
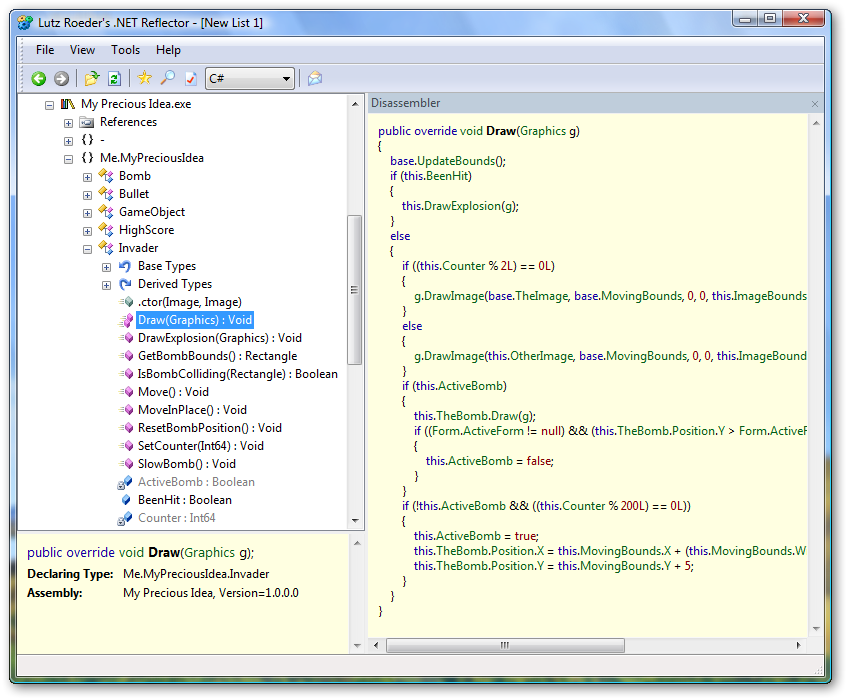
As you can see in the screenshot above, all application sources can be easily obtained just with several mouse clicks! If your product is not obfuscated then hackers have a huge possibilities to tamper with product features. Unsavory competitors may even copy & paste parts of your code for use in their own products.