Security Architecture
The architecture of a security system is based on users and groups of users. The following illustration shows how users and local and global groups in Microsoft® Windows NT® 4.0 and Windows® 2000 can map to security accounts in Microsoft SQL Server™, and how SQL Server can handle security accounts independently of the accounts in Windows NT 4.0 and Windows 2000.
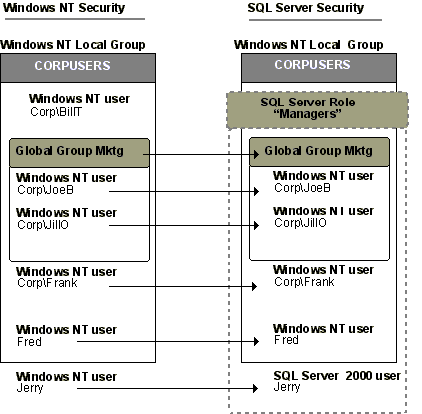
The CORPUSERS local group contains two users and a global group, Mktg, which also contains two users. SQL Server allows Windows NT 4.0 and Windows 2000 local and global groups to be used directly to organize its user accounts. Additionally, the Windows NT 4.0 users Fred and Jerry, not part of a Windows NT 4.0 group, can be added to an instance of SQL Server either directly as a Windows NT 4.0 user (Fred for example), or as a SQL Server user (Jerry).
SQL Server extends this model further with the use of roles. Roles are groups of users organized for administrative purposes, like Windows NT 4.0 or Windows 2000 groups, but are created in SQL Server when an equivalent Windows NT 4.0 or Windows 2000 group does not exist. For example, the Managers role contains the Windows NT 4.0 Mktg global group and the Windows NT 4.0 users Frank and Fred.
SQL Server also provides security at the application level through the use of individual database application roles.
For more information, see the Windows NT 4.0 or Windows 2000 documentation.