|
CPU_CTRL_XMC1
|
Usage
The below example illustrates how to use the exceptions settings using XMC1400 board.
Required Hardware
XMC1400 board
Instantiate the required APPs
Drag the CPU_CTRL_XMC1 APP. Update the fields in the GUI of this APP with the following configuration.
Example: Access invalid address Hard fault exceptions have various reasons:
- Execution of unknown opcodes
- Trying to access invalid address
- Trying to read or write to an on-chip peripheral with disabled access using PAU.
- Stack corruption
- Trying to switch to ARM state
In this example, a HardFault exception is trigger due to an invalid address access. To analyze and find the offensive code, the CPU_CTRL_XMC1 is used. The APP is configured to generate a hard fault handler with debugging capabilities. These debugging capabilities allow the user to decode the stack at the moment of the exception and in most of the case find the root cause for the exception.
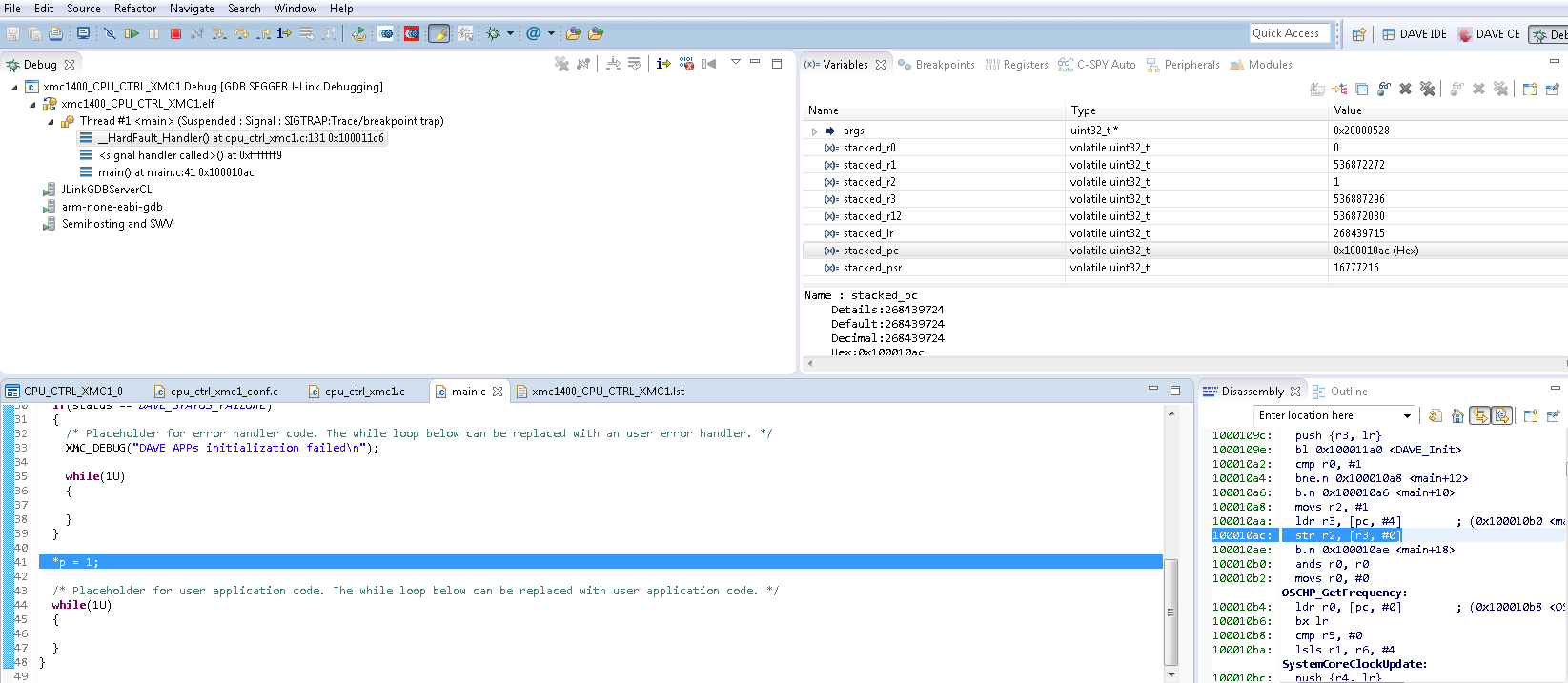
The code that injects the fault looks like:
int32_t *p = (int32_t *)0x20004000U; *p = 1;
The code is trying to access via a pointer over the RAM region. This a actual code can be due to an overflow in a pointer. After executing the code, the breakpoint in the hardfault handler will stop the execution. The stacked PC can help us to identify the offensive code.
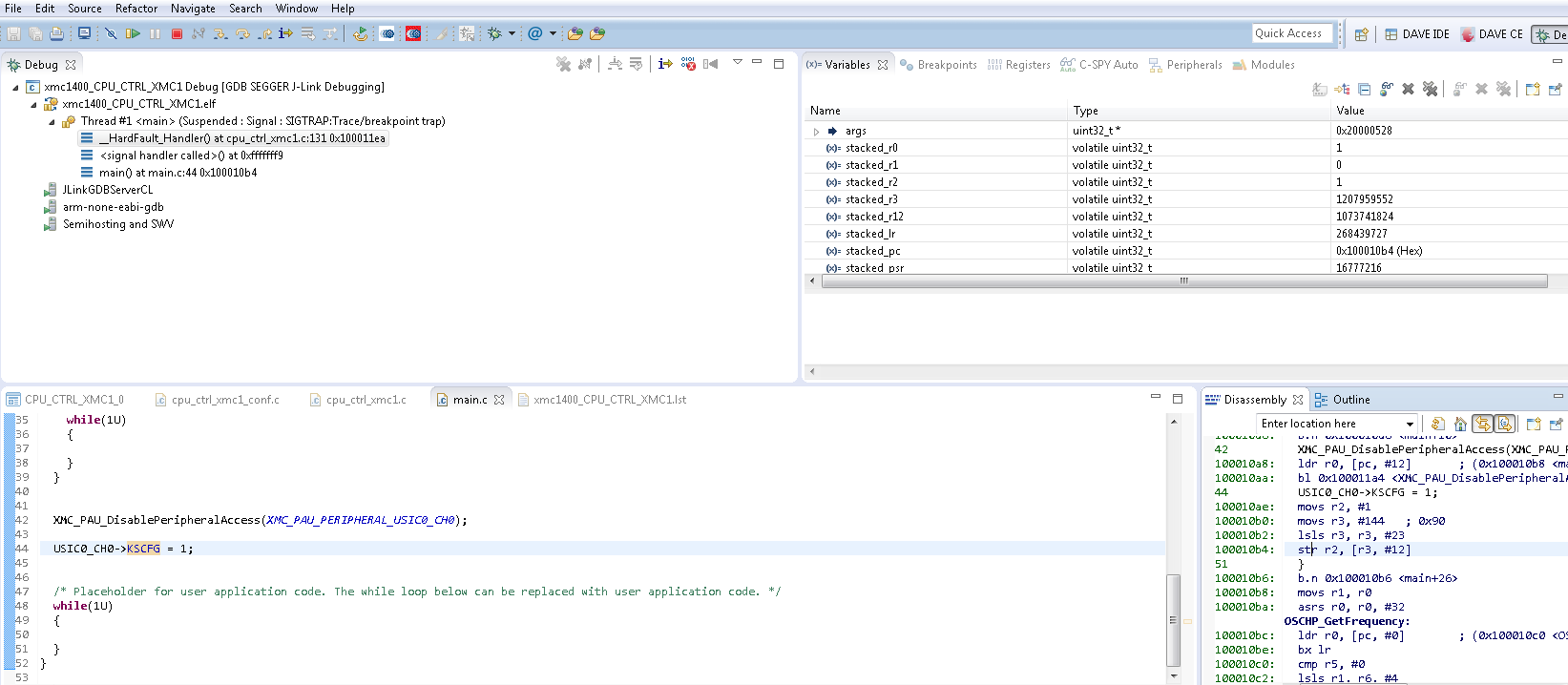
The stacked PC is pointing to the code where the invalid address was used. Example: Access peripheral disabled by PAU In this example we try to access a peripheral which previously has been disabled by the application.
The following code will trigger a hardfault:
XMC_PAU_DisablePeripheralAccess(XMC_PAU_PERIPHERAL_USIC0_CH0); USIC0_CH0->KSCFG = 1;
The stacked PC points to the offensive code.